Be Aware of Android Online Banking Trojan
SOVA
A mobile banking malware is targeting the customers in Indian cyberspace using SOVA android Trojan with the ability to harvest credentials (usernames and passwords) for ransom through overlay attacks by taking advantage of Android's Accessibility services.
The malware hides itself within fake android applications displaying feature logos of legitimate applications like Amazon and Google Chrome to deceive users into installing them. The SOVA Trojan upgraded its capabilities to target nearly 200 mobile applications, including banking apps, crypto exchanges and wallets.
Dangers of the Trojan: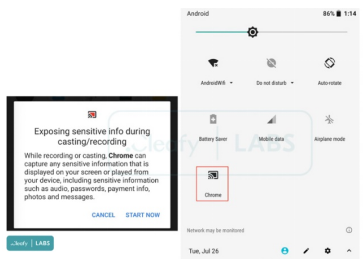
- Captures the credentials of net banking apps and access bank accounts
- Intercept two-factor authentication (2FA) codes
- Steal cookies,
- Capture keystrokes,
- Takes screenshots
- Records video
- Perform gestures like screen click, swipe etc.
- May lead to large-scale financial frauds
Modus operandi
- Trojan will be installed /distributed via message
- Send details of applications installed on the device
- Communicate with command and control server
Advisory:
- Download applications only from trusted sources like legitimate websites or authorized app store i.e manufacturer of device or Operating System app store
- Avoid downloading apps from SMS, emails, social media messages, or by clicking advertisements.
- Be cautious about allowing any new permissions during the installation of the applications.
- Properly verify the app details in the developer’s website before downloading it.
- Avoid installing the apps that have typo graphical/ grammatical mistakes in its descriptions
- Pay attention to reviews and comments of the users, developer details, number of downloads etc., before installing any of the applications.
- Use a trusted anti-virus software for Mobile Security to stay safe from Android malware.
- Avoid installing mobile applications which contains advertisements
- Check and install regular Android updates and patches

